The post Boost Jenkins pipelines with Red Hat Advanced Developer Suite showed how Red Hat Developer Hub and its one-click Software Templates can transform a developer’s first week on the job from a ticket marathon into a 2-minute bootstrap. It described how a brand-new Jenkinsfile, a Red Hat OpenShift Dev Spaces workspace, and a CI pipeline are created automatically to help teams can innovate at full speed.
But velocity alone isn’t a win if an attacker can infiltrate that same pipeline. In this follow-up post, we’ll focus on a different aspect: you’ll harden the very Jenkins flow you spun up in part 1 by adding cryptographic signing, SBOM validation, and runtime enforcement—all without reinstating ticket ping-pong.
Note
If you missed the previous post, hit pause and read that first; it sets up the framework we’re about to secure.
Ready? Let’s move from fast to faster and safer.
The pipeline at a glance
Figure 1 shows the usual developer motions from left to right—commit, build, test, deploy—but each hand-off now carries cryptographic proof and policy assurance:
- A commit is signed as it leaves the laptop.
- The CI verifies the signature before any build logic runs.
- The container image is built and then signed with Red Hat Trusted Artifact Signer.
- A Software Bill of Materials (SBOM) is generated and analyzed using Red Hat Trusted Profile Analyzer for CVEs and license risk.
- The image is pushed to Red Hat Quay, scanned again, and finally admitted to the cluster only if Red Hat Advanced Cluster Security confirms everything is in order.
- Policy gate halts the pipeline if signatures or SBOM checks fail.
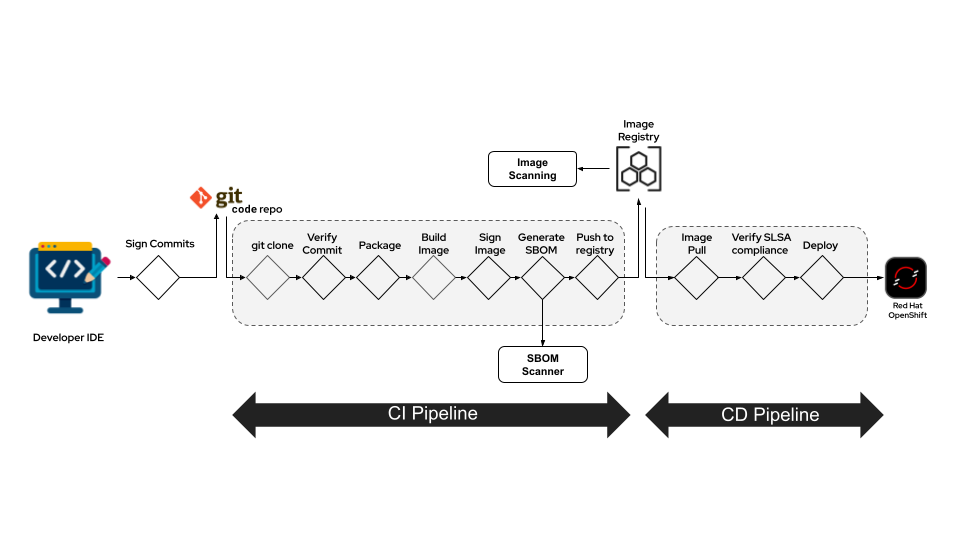
Teams maintain velocity, and trust is enforced.
Meet the security line-up
The Red Hat Advanced Developer Suite adds 3 heavyweight security services into Jenkins with almost no extra configuration:
- Red Hat Trusted Artifact Signer generates and manages cryptographic keys, then signs every image and commit, recording in-toto provenance.
- Red Hat Trusted Profile Analyzer ingests Software Bills of Materials (SBOMs), checks them against CVE and license risks, and returns a pass/fail verdict.
- Conforma (formerly Enterprise Contracts) ties signatures and SBOM verdicts together, blocking non-compliant artifacts before the pipeline continues.
These services are complemented by 2 powerful tools:
- Red Hat Quay: An enterprise registry that scans, stores, and serves only trusted images.
- Red Hat Advanced Cluster Security for Kubernetes: Runtime security, vulnerability scanning, and policy enforcement so that only signed trusted images make it to production.
Together, they help create an unbreakable chain of custody from commit to Kubernetes scheduler.
Wiring the guardrails into Jenkins
Red Hat Advanced Developer Suite weaves its security guardrails into the toolchain you already run—Jenkins jobs, GitOps workflows, and container registries—through containerized services, REST APIs, and drop-in plug-ins.
At build time, Red Hat Trusted Artifact Signer adds cryptographic signatures and in-toto provenance with a single pipeline step. The resulting image’s Software Bill of Materials is then fed to Red Hat Trusted Profile Analyzer, which evaluates CVEs, licenses, and custom policies before the job can advance.
All verdicts stream back to Red Hat Developer Hub, giving developers and platform teams one portal to trigger builds, observe guardrails in action, and trace every artifact on its path to production. This delivers cryptographic trust and real-time risk insight without forcing a pipeline rewrite or slowing release velocity.
We used the following Jenkins file to include those security guardrails:
pipeline {
agent any
environment {
IMAGE = 'quay.io/demo/wealthwise-backend:latest'
SBOM_ID = "wwb-${BUILD_NUMBER}"
TAS_KEY = credentials('cosign-key')
TPA_TOKEN = credentials('rhtpa-token')
ACS_TOKEN = credentials('rhacs-token')
TPA_URL = 'https://rhtpa.demo'
}
stages {
stage('Clone source code') {
steps { sh 'git clone https://gitlab.com/rhpds/app.git' }
}
stage('Verify commit') {
steps { sh 'gitsign verify --certificate-identity=<email> --certificate-oidc-issuer=<issuer-url>' }
}
stage('Build & Unit Test') {
steps { sh 'mvn clean package -DskipTests' }
}
stage('Containerise & Push') {
steps { sh """
podman build -t $IMAGE .
podman push $IMAGE
"""}
}
stage('Sign Image (RHTAS)') {
steps { sh "cosign sign --key \$TAS_KEY \$IMAGE" }
}
stage('Generate & Upload SBOM (RHTPA)') {
steps { sh """
syft $IMAGE -o json > sbom.json
curl -H 'Authorization: Bearer $TPA_TOKEN' \
-H 'Content-Type: application/json' \
--data @sbom.json \
$TPA_URL/api/v1/sbom?id=$SBOM_ID
"""}
}
stage('Enterprise-Contract Gate') {
steps { sh """
enterprise-contract verify image \
--image \$IMAGE \
--public-key ${TAS_KEY}.pub \
--policy git::github.com/demo/policies//base
"""}
}
stage('RHACS Admission Check') {
steps { sh """
export ROX_API_TOKEN=$ACS_TOKEN
roxctl image check \$IMAGE
"""}
}
}
}The previous Jenkins file shows where each Advanced Developer Suite control plugs in and explains why it matters. Let’s walk through it from top to bottom so the purpose of every stanza is crystal clear.
In the Environment block, we declare the image tag, an SBOM ID, and three secrets that Jenkins pulls from its credential store: TAS_KEY for Cosign signing, TPA_TOKEN for talking to Trusted Profile Analyzer, and ACS_TOKEN for the final runtime gate. These variables are set once by the platform team; developers never see the keys themselves.
We then define the pipeline stages:
- Clone source code: Clone the source code into the workspace
- Verify commit: Verify that the latest commit was signed by a trusted source
- Build and unit test stage: Classic Maven compile. Nothing specific to Red Hat Advanced Developer Suite here—just good old CI doing its job.
- Containerize and push: We use
podman buildto create the image and immediately push it to Quay. At this point the image exists, but it’s not yet trusted. - Sign image (Trusted Artifact Signer): One line of Cosign gives the image a cryptographic signature plus an in-toto provenance file. If an attacker later swaps the image, the signature check will fail and the pipeline won’t proceed.
- Generate and upload SBOM (Trusted Profile Analyzer): We produce a Software Bill of Materials, then a cURL call uploads that SBOM to the Analyzer service. The Analyzer inspects the manifest for CVEs, license risk, and custom policy, and then records the verdict against the SBOM ID.
-
Enterprise-contract gate: This CLI ties the two earlier steps together. It verifies that:
- The cryptographic signature is valid and points to the correct public key.
- The analyzer gave the SBOM a “pass.”
If either check fails, Jenkins marks the build unstable—long before anything ships.
- Advanced Cluster Security admission check: Even after the build clears all earlier gates, Advanced Cluster Security runs one last policy check at cluster-admission time. Think of it as the bouncer who verifies the ID again before letting the container onto the dance floor.
From the developer’s perspective the pipeline still feels familiar—build, test, push, deploy—but beneath the surface, every handoff now carries cryptographic proof and policy compliance. That’s the value of Red Hat Advanced Developer Suite: security is integrated into your existing CI flow, not added on as an afterthought.
Embedding the secure pipeline in a Software Template
Platform engineers wrap that Jenkinsfile into a Software Template in Developer Hub, adding just two extra fields to the template’s parameters: block—cosignKey and rhtpaToken. Developers still fill out a 1-page form, click Create, and get the same friction-free repo as before, only now the pipeline is signed, scanned, and policy-enforced by default.
No extra PRs, no nightly checklist, no Slack chasers.
Real-world impact
Industry pilots that pair developer-velocity tooling with supply-chain guardrails typically show 3 clear trends (figures aggregated from Red Hat field engagements and customer briefings, 2024-2025):
- ~30% faster cycle times once security checks are moved from out-of-band spreadsheets into automated pipeline stages.
- Up to 40% fewer audit exceptions when SBOM validation and policy enforcement run on every build instead of at release time.
- Zero unsigned images in production wherever signature verification is enforced by admission controllers such as Enterprise Contract or Advanced Cluster Security.
The takeaway is consistent: you can keep your delivery velocity and dramatically lower risk when security becomes code, not a checklist.
Conclusion
Velocity without trust is a gamble. By adding Red Hat Trusted Artifact Signer, Red Hat Trusted Profile Analyzer, Red Hat Quay, and Red Hat Advanced Cluster Security to an ordinary Jenkinsfile, you weld proof and policy into every artifact—without slowing teams down.
Ready to try it yourself?
- Revisit part 1, Boost Jenkins pipelines with Red Hat Advanced Developer Suite, to see how the pipeline scaffolding is generated in seconds.
- Explore the full Red Hat Advanced Developer Suite.
- Get hands on with Red Hat Trusted Artifact Signer.
- Analyze your own SBOMs using Red Hat Trusted Profile Analyzer.
Move fast, deliver with confidence, and let the guardrails do the heavy lifting.
The post How to secure your Jenkins pipeline with Red Hat Advanced Developer Suite appeared first on Red Hat Developer.



