Breaches continue to grow in scale and speed, yet the weakest point remains unchanged: people. According to Dune Security’s 2025 CISO Risk Intelligence Survey, over 90 percent of incidents still originate from user behavior rather than technical flaws. The survey results show that attackers have shifted their methods and that enterprise defenses are struggling to keep pace.

### Attacks move beyond email
While every enterprise surveyed simulates email phishing, most stop there. Attackers have expanded into channels that security teams rarely monitor or test, such as encrypted messaging apps, SMS, voice calls, and collaboration platforms.
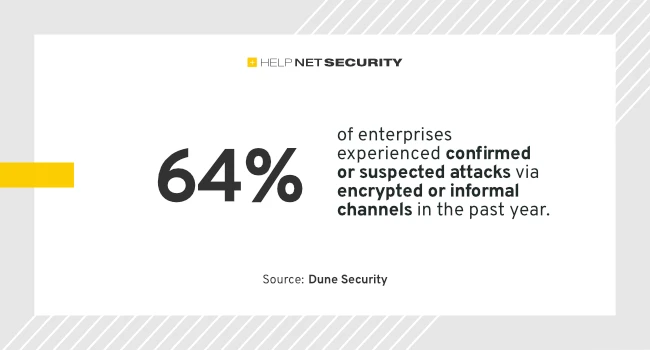
Sixty-four percent of organizations confirmed a malicious social engineering attempt through encrypted or informal channels in the past 12 months. None of the surveyed CISOs reported simulating attacks over WhatsApp, Signal, or similar apps. Confidence in employees spotting threats there is also very low.
“Attackers are exploiting the blind spots where enterprises aren’t defending,” said David DellaPelle, CEO of Dune Security. “Legacy SAT programs are limited to yesterday’s email threats while real breaches now start in high-trust, low-visibility channels like encrypted messaging, SMS, voice call, and deepfake-based impersonation.”
This gap leaves attackers with wide latitude to exploit trust in channels that feel routine and internal. Fake executive messages on Teams, spoofed IT support in Slack, or urgent voice calls now bypass technical defenses by targeting behavior directly.
### Simulation and training are misaligned
Most organizations test basic phishing, but just 18% tailor simulations by both user role and behavior, even though 91% of CISOs believe they should. The lack of personalization limits the value of awareness efforts, especially as attackers refine their tactics with AI-generated messages that mimic tone, workflow, and urgency.
Behavioral simulation data reinforces this point. In controlled phishing scenarios, AI-personalized emails drove three times more user interaction than traditional templates. Of those who clicked, 30% went on to submit MFA credentials, showing how deeply compromise can extend once initial trust is gained.
Despite universal email testing, only 26% of CISOs say they have high confidence in their users’ ability to detect phishing in real conditions.
### Insider threat is broadening
The survey also reveals a shift in how insider risk is defined. Traditional malicious insiders remain a concern, but compromised and negligent users are now equally significant. Manipulated employees, often pressured over unmonitored apps, have become a preferred entry point for attackers.
Many security leaders don’t feel prepared to handle insider threats, and they acknowledge gaps around mobile devices, collaboration tools, and encrypted messaging. Without proper monitoring and practice in these areas, insider attacks often go unnoticed until it’s too late.
### CISOs struggle with execution, not awareness
Security leaders largely agree on the nature of the problem. Just 6% cite lack of executive buy-in as a barrier. Instead, the obstacles are operational: difficulty measuring user-level risk, lack of staff capacity, and reliance on legacy tools that fail to reflect real-world attack vectors.
Thirty-six percent of CISOs identify risk measurement as their top barrier, while another third point to limited resources. Outdated training platforms are another source of frustration. Only 12% believe their current awareness programs are sufficient, and more than a third disagree outright.
According to Dune Security’s 2025 CISO Risk Intelligence Survey, over 90 percent of incidents still originate from user behavior rather than technical flaws.
The survey results show that attackers have shifted their methods and that enterprise defenses are struggling to keep pace.
Attackers have expanded into channels that security teams rarely monitor or test, such as encrypted messaging apps, SMS, voice calls, and collaboration platforms.
Sixty-four percent of organizations confirmed a malicious social engineering attempt through encrypted or informal channels in the past 12 months.
Thirty-six percent of CISOs identify risk measurement as their top barrier, while another third point to limited resources.
Breaches continue to grow in scale and speed, yet the weakest point remains unchanged: people. According to Dune Security’s 2025 CISO Risk Intelligence Survey, over 90 percent of incidents still originate from user behavior rather than technical flaws. The survey results show that attackers have shifted their methods and that enterprise defenses are struggling to keep pace.
Attacks move beyond email
While every enterprise surveyed simulates email phishing, most stop there. Attackers have expanded into channels that security teams rarely monitor or test, such as encrypted messaging apps, SMS, voice calls, and collaboration platforms.
Sixty-four percent of organizations confirmed a malicious social engineering attempt through encrypted or informal channels in the past 12 months. None of the surveyed CISOs reported simulating attacks over WhatsApp, Signal, or similar apps. Confidence in employees spotting threats there is also very low.
“Attackers are exploiting the blind spots where enterprises aren’t defending,” said David DellaPelle, CEO of Dune Security. “Legacy SAT programs are limited to yesterday’s email threats while real breaches now start in high-trust, low-visibility channels like encrypted messaging, SMS, voice call, and deepfake-based impersonation.”
This gap leaves attackers with wide latitude to exploit trust in channels that feel routine and internal. Fake executive messages on Teams, spoofed IT support in Slack, or urgent voice calls now bypass technical defenses by targeting behavior directly.
Simulation and training are misaligned
Most organizations test basic phishing, but just 18% tailor simulations by both user role and behavior, even though 91% of CISOs believe they should. The lack of personalization limits the value of awareness efforts, especially as attackers refine their tactics with AI-generated messages that mimic tone, workflow, and urgency.
Behavioral simulation data reinforces this point. In controlled phishing scenarios, AI-personalized emails drove three times more user interaction than traditional templates. Of those who clicked, 30% went on to submit MFA credentials, showing how deeply compromise can extend once initial trust is gained.
Despite universal email testing, only 26% of CISOs say they have high confidence in their users’ ability to detect phishing in real conditions.
Insider threat is broadening
The survey also reveals a shift in how insider risk is defined. Traditional malicious insiders remain a concern, but compromised and negligent users are now equally significant. Manipulated employees, often pressured over unmonitored apps, have become a preferred entry point for attackers.
Many security leaders don’t feel prepared to handle insider threats, and they acknowledge gaps around mobile devices, collaboration tools, and encrypted messaging. Without proper monitoring and practice in these areas, insider attacks often go unnoticed until it’s too late.
CISOs struggle with execution, not awareness
Security leaders largely agree on the nature of the problem. Just 6% cite lack of executive buy-in as a barrier. Instead, the obstacles are operational: difficulty measuring user-level risk, lack of staff capacity, and reliance on legacy tools that fail to reflect real-world attack vectors.
Thirty-six percent of CISOs identify risk measurement as their top barrier, while another third point to limited resources. Outdated training platforms are another source of frustration. Only 12% believe their current awareness programs are sufficient, and more than a third disagree outright.


