On the Stormcast, Johannes talked about BASE64 and DNS used by a backdoor.
I was interested to learn more about this, because DNS labels can only contain letters, digits and a hyphen. If you make a distinction between uppercase and lowercase letters, you have exactly 63 characters to choose from. While BASE64 requires 64 characters (and a 65th character for padding: =).
So how can the backdoor use BASE64 in a label, since RFC 1035 (and updates) does not allow characters +, / and = ?
I did some tests.
I had my dnsresolver.py tool running on a server, configured to answer DNS A requests for label Aa0+/=.
And it just worked:
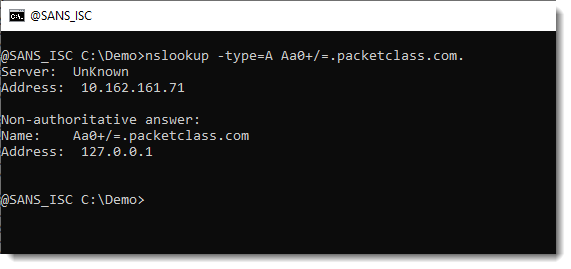
nslookup doesn’t check the format of the labels, and neither did the DNS servers that forwarded my queries to my dnsresolver.py tool.
But the Windows APIs that help with resolving hostnames, do care about the format.
For example, the ping tool that uses the Windows API, doesn’t work:
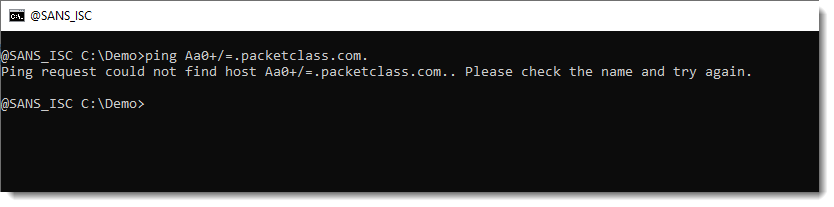
Neither does the DnsApi:
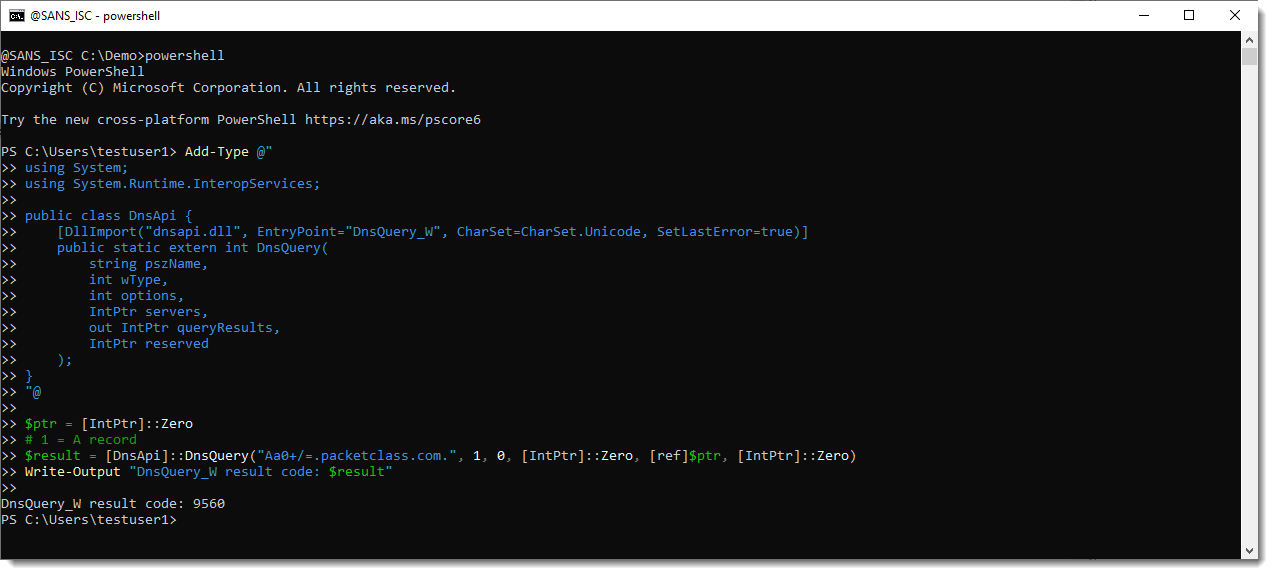
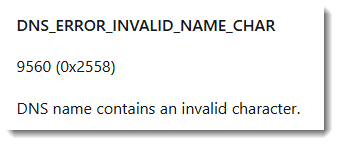
Error 9560 is because of the +, / and = characters I used:
Thus malware can use special characters in DNS labels as a C2 channel, but then it has to talk directly to the DNS server (like nslookup does), it can’t use Windows APIs to achieve this.
It might be interesting to check your DNS logs (if you have them) for labels with special characters. It’s something I’ll investigate and report later.
Didier Stevens\
Senior handler\
blog.DidierStevens.com
On the Stormcast, Johannes talked about BASE64 and DNS used by a backdoor.
I was interested to learn more about this, because DNS labels can only contain letters, digits and a hyphen.
If you make a distinction between uppercase and lowercase letters, you have exactly 63 characters to choose from.
So how can the backdoor use BASE64 in a label, since RFC 1035 (and updates) does not allow characters +, / and = ?
It might be interesting to check your DNS logs (if you have them) for labels with special characters.
On the Stormcast, Johannes talked about BASE64 and DNS used by a backdoor.
I was interested to learn more about this, because DNS labels can only contain letters, digits and a hyphen. If you make a distinction between uppercase and lowercase letters, you have exactly 63 characters to choose from. While BASE64 requires 64 characters (and a 65th character for padding: =).
So how can the backdoor use BASE64 in a label, since RFC 1035 (and updates) does not allow characters +, / and = ?
I did some tests.
I had my dnsresolver.py tool running on a server, configured to answer DNS A requests for label Aa0+/=.
And it just worked:

nslookup doesn’t check the format of the labels, and neither did the DNS servers that forwarded my queries to my dnsresolver.py tool.
But the Windows APIs that help with resolving hostnames, do care about the format.
For example, the ping tool that uses the Windows API, doesn’t work:

Neither does the DnsApi:

Error 9560 is because of the +, / and = characters I used:

Thus malware can use special characters in DNS labels as a C2 channel, but then it has to talk directly to the DNS server (like nslookup does), it can’t use Windows APIs to achieve this.
It might be interesting to check your DNS logs (if you have them) for labels with special characters. It’s something I’ll investigate and report later.
Didier Stevens
Senior handler
blog.DidierStevens.com